How Do I Know Which Standard an Rfid Card Uses
Hotels use keycards to authorize their guests only to access their hotel room and the fitness center set to stop working the morning of checkout This system allows management to restrict employee access only to specific authorized. It would have been nice if.

02 07 2017 Rfid Vs Nfc What Is The Difference
NFC and RFID Card Types General RFID cards and more particularly NFC cards are used very commonly in access control and mobile payment the.
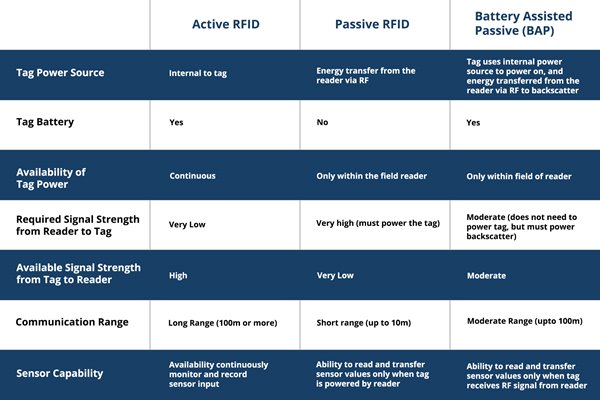
. If you see the marked symbol on the image below it is supporting RFID. 2 Helpful Answer Positive Rating Jan 2 2011 Not open for further replies. There is a device that reads information contained in a wireless device or tag from a distance without making any physical contact or requiring a line of sight.
Most tags currently being used contain around 256 bits of storage about the equivalent 6 phone numbers. And the 40 bits the ID-20 returns from EM4100 tags do not match in any way what is printed on the cardtags or is read by the USB reader. RFID-enabled cards have a logo.
The location on the card sector file application The programming format. Not very easy to do. Although each RFID chip reader is different RFID chips will generally emit a frequency that will cause the chip reader to produce a beeping noise to.
Youll usually be able to tell if a credit card is RFID-enabled by the contactless symbol on the front or back of the card - it looks like a sideways WiFi symbol. When combi cards are used there are two parts of the card that need to be programmed. NFC is 1356 MHz RFID your gym card is either 1356 MHz aka high frequency HF RFID or it could be older technology low frequency LF RFID.
The RFID card can be used for identification and the triggering of an event on any RFID reader. RFID technology has been commercially available in one form or another since the. To find out whether a credit card has an RFID chip you can look at the card to tell if it does or does not.
Most of these door access RFID cards have the antennas running the entire perimeter of the physical card. Few ways you can tell if its LF or HF. A frequency is like any of the numbers on your radio dial.
In addition to a unique ID many tags can also store further data. What kind of information can be stored on a tag. You tune into a specific frequency to listen to your favorite station.
The plastic body of the card has an antenna embedded on it. A secure microprocessor is embedded on the chip which has an internal memory. The number range and potentially the facility code.
But I do know the numbers programmed into the EM4100 cards and tags--theyre printed on the cards plus I bought a cheap EM4100 USB RFID reader and it returns the printed numbers just fine. I pretty sure the key card is a RFID card like some security badges. The phone unlock certainly does not use NFC and theres no way to clone an NFC card with a phone.
Zaiksas Z Zaiksas Points. RFID cards work in a similar manner using 1356 Mhz megahertz125 Khz kilohertz or UHF 860-960 Mhz. So you cant just trip it like a SIM card.
Java Cards use an application structure. As you enter customs the RFID chip in your passport is scanned by a lintechtt designed to read your biophysical information embedded in the chip and present it to the customs. Over 40 Years of Superior Service and Offering Products from Over 2000 Suppliers.
Its important to note that just because a credit card has a visible chip - called an EMV chip - doesnt mean it has RFID capability. The phone unlock uses Bluetooth and has nothing to do with the card. For example you might listen to 933 or 1015 FM.
Most ticketing cards are using the Mifare based on ISOIEC 14443A standard. Times the standard read range. I believe the card does use NFC but NFC is just a particular implementation of RFID.
Answer 1 of 2. The memory can store and send data an example is your passport. Ad Digi-Key is the Franchised Distributor for all Your RFID Products.
A number of these cards also behave differently. An RFID key card can be programmed to open only specific doors or only one for a specific amount of time. The data inside an RFID Smart Card is encoded in a chip.
RFID cards communicate through radio waves using one of three frequencies. Do RFID cards really work. If purchased together with Zipabox and Zipato Mini RFID keypad it can be used to arm and disarm a security system or to run any automation scenario in the Zipato Cloud environment.
RFID chips are simple systems made from a silicon memory chip coupled to a transceiver. Radio Frequency Identification RFID technology uses radio waves to identify people or objects. Generally with HF read distance is 1 to 2 cm whereas LF can go up to 4 cm.
To tell if your card is an NFC card you merely need to look for the NFC signal on it which looks like this. Does my credit card have RFID. You may want to check with a contactless reader or check for the coil resonance about 17-19 MHz with a grid dipper or other suitable instrument.
Turn on the RFID chip reader and scan the vicinity of the area you believe RFID chips are present. US 392 -. Also if the card says PayPass payWave or blink it also has RFID capabilities.
If youre not sure whether your card is RFID enabled you can easily check by taking a look at the card. Anything that can be represented by a number. In short to program any card you will need to know.
Once its close to the readers antenna the chip transmits the information identifying the user to a computerized security system. Often this data can be reprogrammed.

Rfid Basics Part I What Is Rfid Rfid Tags And Labels Types Of Rfid Tags Youtube
Mifare Cards Rfid Cards Other Contactless Cards At Low Prices Cardzgroup

Mid Range Rfid Epc Class 1 Gen 2

Different Types Of Rfid Systems
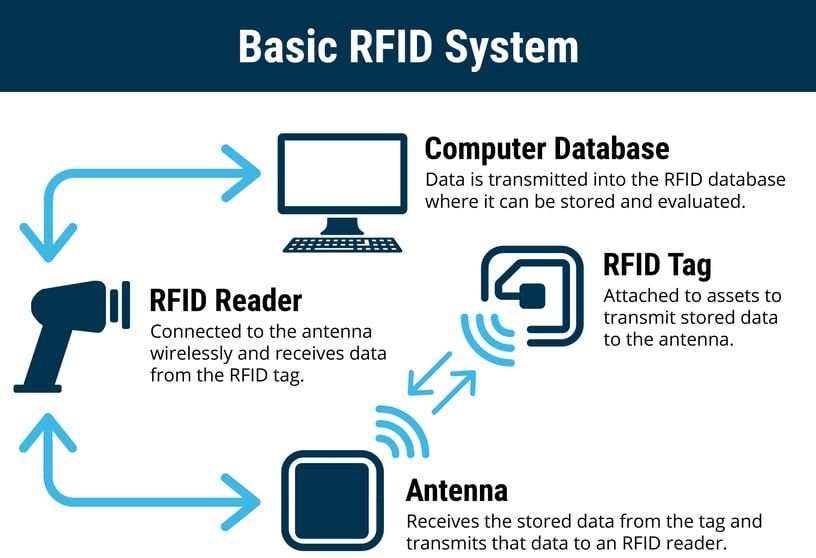
Rfid The Technology Making Industries Smarter
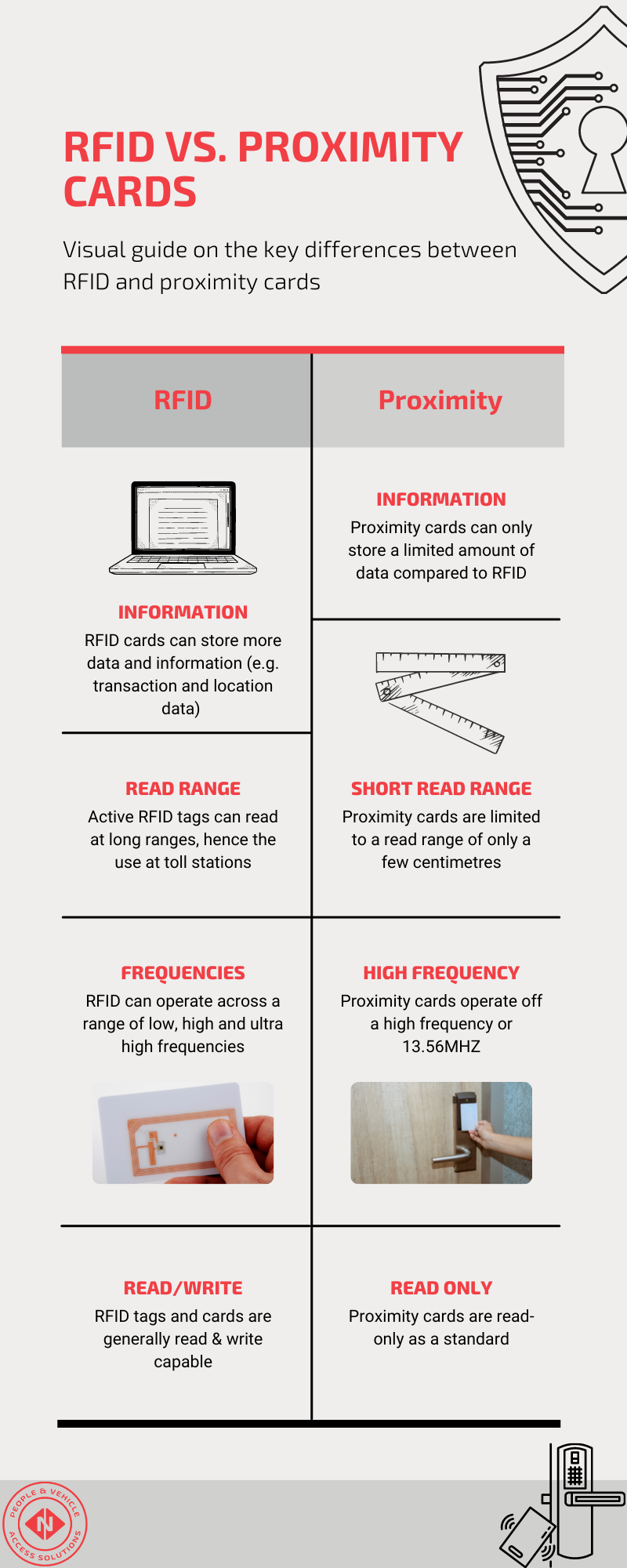
5 Differences Between Rfid Cards And Proximity Cards Simple Guide

Rfid Technology What It Is And How To Use It In Your Store 2022
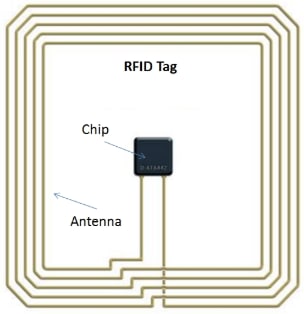

Comments
Post a Comment